Cybersecurity Alert - Ongoing Phishing Campaign Impersonating FINRA Employees
IMPACT: All Firms
Member firms should be aware of an ongoing phishing campaign involving fraudulent emails targeting executives purporting to be from FINRA employees, with the goal of harvesting credentials. These emails are not from FINRA, and firms should delete them and consider blocking the fraudulent domains. The Alert further describes the campaign and includes recommendations for members to identify the fraudulent emails to mitigate the threat.
Background
As early as March 3, 2025, a phishing campaign began targeting executive employees including broker-dealers, investment advisors, wealth management entities and private equity firms, alleging FINRA employees are attempting to collect information about mismanaged client investments.
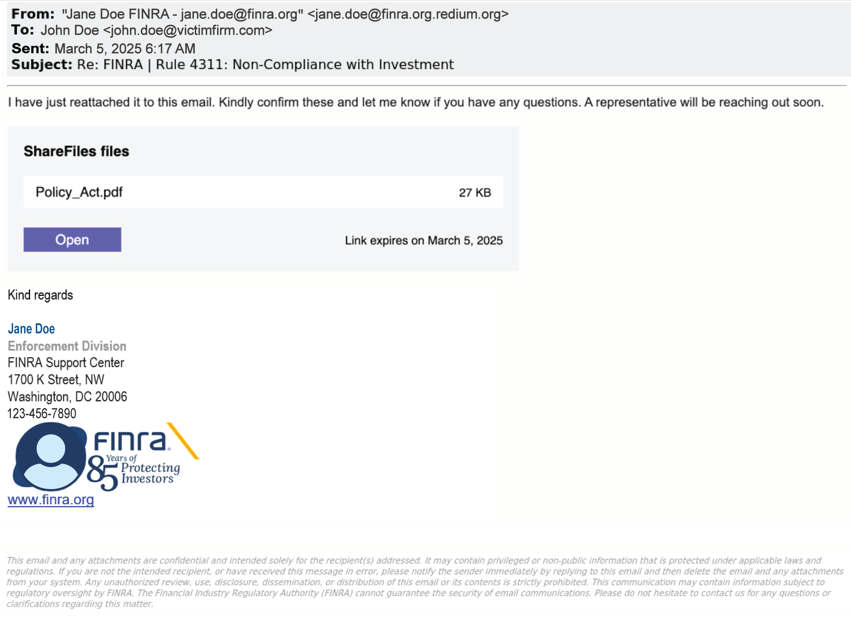
The campaign varies from a single email to multiple emails. In all cases, an initial email containing the subject line “RE: FINRA | Rule 4311: Non-Compliance with Investment” asked the intended victim to confirm if a previous email was received “regarding the mismanagement of client assets.” The email signature block contained the name of a real FINRA employee along with their LinkedIn profile picture, all of which has been masked in the example below.

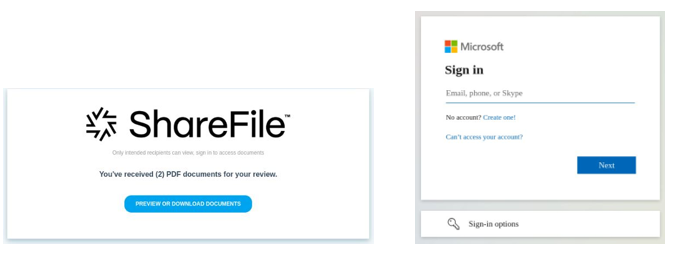
Some intended victims responded to the imposter’s first email causing them to receive a follow-up email which included a link to retrieve a pdf file with more details about the “mismanaged client assets.” The link directed the user to a file-sharing site to open the pdf file with a notice that the link expires on the same date of the email. When a victim clicked the “Open” button, the user was redirected to a HubSpot "ShareFiles” website, a legitimate service which can be used for running email marketing campaigns and document sharing.
Analysis
A graphic on the “ShareFile” page advised the victim that “Only intended recipients can view, sign in to access documents” with a notice that, “You’ve received (2) PDF documents for your review.” There was a button to click to Preview or Download Documents (hosted on HubSpot at hsforms[.]com). When the victim clicked the preview or download button, they were redirected to a fraudulent page designed to resemble a Microsoft Sign-in page (hosted at ati4s[.]com), where the threat actor harvested the credentials.
The imposter crafted the emails to appear they came from a FINRA employee by using a display name (also known as a “vanity name” or “email alias”) that included the employee’s first and last name, followed by “FINRA.”
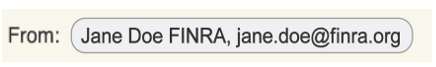
By manipulating the display name, the threat actor mimicked the legitimate FINRA email address while hiding the actual email address behind the fraudulent domain. Victims would need to closely examine the full email address to identify the true sender.

Examining the fully expanded email address in the header of the email message revealed the email address was from an imposter using a fully qualified domain name containing the subdomain finra[.]org. The threat actor configured the domain to leverage Google’s flexible email hosting services.

Reviewing the messaging campaign, the initial email encouraged email interaction with the fraudster, and the subject line attempted to deceive the victim into thinking they missed a previous email message. In the follow-up email example above, the threat actor added a sense of urgency to retrieve the ShareFiles pdf by providing an expiration date (i.e., the same day as the email) for access.
Based on FINRA’s assessment of prior phishing campaigns, the threat actors will likely rotate subdomains with legitimate company domains. While the finra[.]org subdomain is active, threat actors could rotate FINRA logos, or names and pictures of legitimate FINRA employees, to continue the phishing campaign and credential theft.
Recommendations to Protect Your Firm
To protect against this email phishing campaign, FINRA recommends the following actions.
- Technology staff at the firm should be alerted to the indicators of compromise:
- redium[.]org
- ati4s[.]com
- Policy_Act.pdf
- hxxps[://]share-na2[.]hsforms[.]com/1JFr7129UQMCsIezpoFRuXA403mgg
- Delete all emails originating from fraudulent domains and URL above.
- Consider blocking the fraudulent domains at the firewall.
- Monitor network traffic for activity related to the URL with the file name.
- Be vigilant for variations of this phishing campaign, including changes in:
- sender name, subdomains, and domains;
- email content and subject lines;
- file names and attachments; and
- suspicious hyperlinks contained within emails.
FINRA reminds firms to verify the legitimacy of any suspicious email prior to responding to it; opening, downloading or previewing any attachments; or clicking on any embedded links. These phishing campaigns may be reported to FINRA by contacting the firm’s Risk Monitoring Analyst or by filing a regulatory tip.
FINRA has requested that the internet domain registrars and hosting providers suspend services for the known malicious domains.
Both the FBI and CISA urge you to promptly report phishing incidents to a local FBI Field Office, the FBI Internet Crime Complaint Center (IC3) at IC3.gov, or CISA via CISA’s 24/7 Operations Center ([email protected] or 888-282-0870).
For questions related to this Alert or other cybersecurity-related topics, contact the FINRA Cyber and Analytics Unit (CAU).
Note: This Alert does not create new legal or regulatory requirements or new interpretations of existing requirements, nor does it relieve firms of any existing obligations under federal securities laws, regulations, and FINRA rules. Member firms may consider the information in this Alert in developing new, or modifying existing, policies and procedures that are reasonably designed to achieve compliance with relevant regulatory obligations based on the member firm’s size and business model. Moreover, some questions may not be relevant due to certain firms’ business models, sizes, or practices.
